About Borg Security
Borg Security is a specialized Web3 cybersecurity firm focused on securing complex infrastructures against hybrid Web2-on-Web3 attack vectors. By blending offensive security tactics with advanced R&D, Borg Security protects users, protocols, and platforms from critical zero-day vulnerabilities and systemic risks in decentralized ecosystems.
Known for working with some of the most prominent names in crypto, Borg Security takes a proactive and highly technical approach to threat detection, penetration testing, and exploit mitigation. Their proprietary tooling and research-first model help Web3 projects identify critical flaws before they become high-impact breaches.
Borg Security is a cutting-edge cybersecurity partner built for Web3. The firm specializes in penetration testing, zero-day exploit mitigation, and offensive research tailored to the unique threat landscape of decentralized platforms. By combining traditional security disciplines with modern onchain intelligence, Borg Security protects user funds, private data, and smart contract ecosystems from emerging attack vectors.
Their work spans a wide variety of attack surfaces, including browser extensions, authentication layers, bridging mechanisms, and complex financial dApps. Whether it's simulating real-world attacks via black-box testing or dissecting application code through white-box audits, Borg Security delivers precision-driven assessments backed by mitigation support, detailed reporting, and re-testing cycles.
Borg's unique focus lies in bridging the gap between Web2 vulnerabilities (like front-end exploits and client-side flaws) and Web3 infrastructure such as smart contracts and signature flows. Their Watchdog monitoring tool—available exclusively to clients—provides real-time threat detection and actionable intelligence to help projects stay one step ahead of attackers.
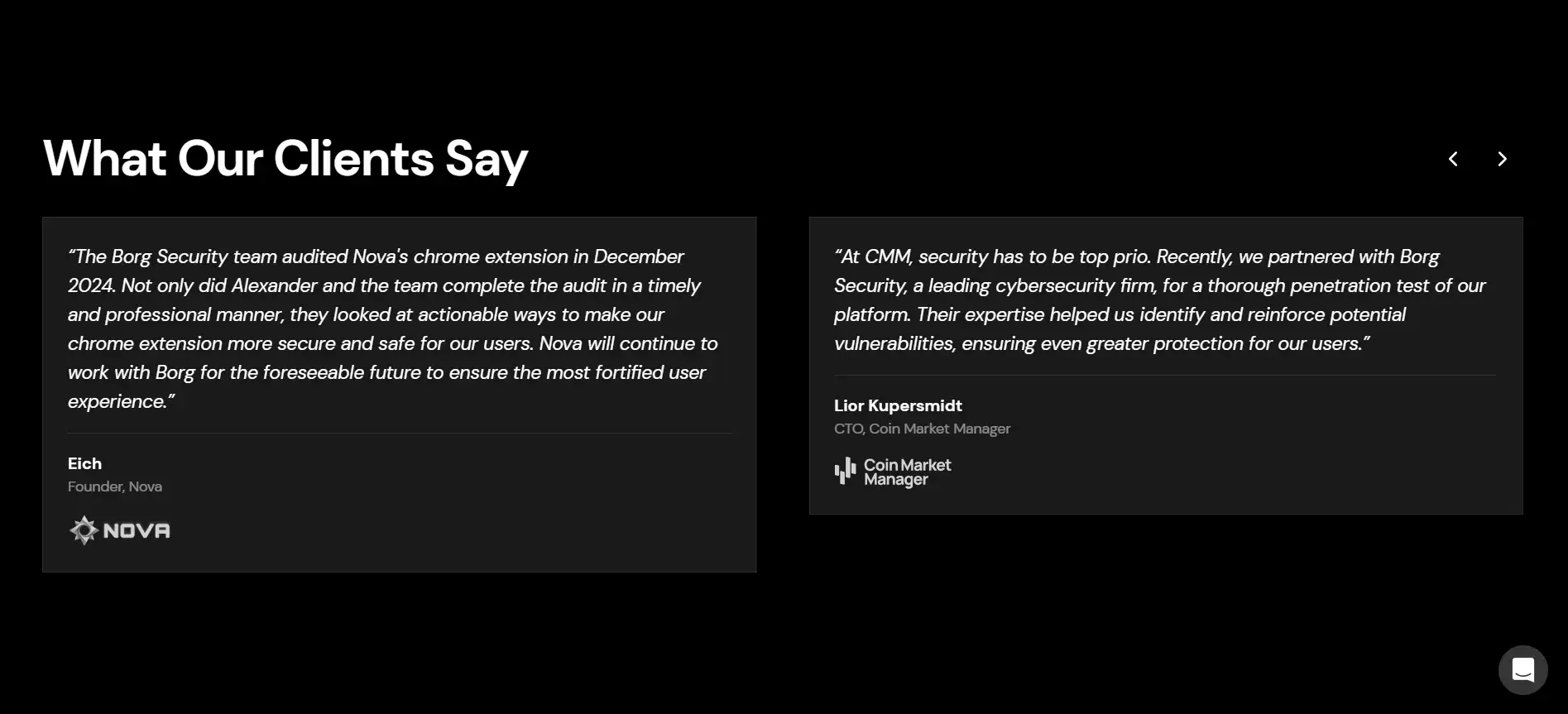
Their client portfolio includes projects across DeFi, algorithmic trading, gaming, and DAO tooling. Highlighted case studies include their work with PRDT.finance, ProphetBots, and Animara World, where they uncovered serious reward manipulation, authentication flaws, and algorithmic trading weaknesses.
Compared to other auditing firms such as Trail of Bits, Halborn, and ConsenSys Diligence, Borg Security brings a deeper offensive research background and a greater emphasis on Web2-connected attack vectors—areas often overlooked by standard smart contract auditors.
Borg Security offers a powerful range of cybersecurity services built specifically for the Web3 era:
- Web2-on-Web3 Penetration Testing: Simulates hybrid exploits using real-world attacker techniques to uncover both smart contract and offchain weaknesses.
- Zero-Day Research & Disclosure: Advanced R&D capabilities allow Borg to discover unknown exploits before they’re weaponized.
- Black Box & White Box Pentests: Provides realistic adversarial simulation (black box) and in-depth code audits (white box) for comprehensive coverage.
- Bug Bounty Triage Services: Expert triage of community-reported vulnerabilities by ex-HackerOne and bug bounty professionals.
- Security Development: Assists teams in implementing secure design patterns, hardened infrastructure, and secure deployment pipelines.
- Strategic Security Consulting: Aligns security strategy with protocol growth plans, helping founders navigate risk while scaling.
- Watchdog Monitoring Tool: An exclusive detection and alerting system that gives real-time insights into system-level threats.
- Battle-Tested Success: Over 17 million users secured, 100+ critical exploits prevented, and 24-hour response times for mitigation.
Getting started with Borg Security is fast, professional, and fully confidential:
- Visit the Site: Go to borgsecurity.io to review services, case studies, and client testimonials.
- Request a Consultation: Use the contact form to share details about your protocol, platform, or infrastructure.
- Scoping & Recon: Borg's team will perform reconnaissance and risk assessment using proprietary tools before outlining a customized engagement plan.
- Testing & Summarizing: Engagement includes black or white-box penetration tests, zero-day analysis, deep attack layers, and detailed reporting with mitigation plans.
- Post-Audit Support: Borg provides re-testing, validation, and advisory assistance to ensure successful remediation of threats.
- Ongoing Monitoring: Eligible clients gain access to Watchdog, a threat monitoring system developed to proactively detect suspicious behaviors.
Borg Security FAQ
Borg Security focuses on Web2-on-Web3 attack vectors, unlike most audit firms that only check smart contract logic. They simulate real-world attacker behavior by combining Web2 penetration testing with smart contract analysis. This hybrid approach uncovers vulnerabilities others miss, making borgsecurity.io a leading choice for high-stakes platforms.
Yes. Borg specializes in identifying client-side, browser extension, and offchain logic flaws—often overlooked in smart contract audits. They replicate real-world exploits like injection attacks, logic bypasses, or reward manipulation that originate in traditional frontends but impact Web3 users and protocols.
Watchdog is Borg Security’s proprietary threat monitoring system, available exclusively to clients. It provides real-time detection and alerting for unusual activity across Web3 applications. Watchdog enhances situational awareness and allows teams to respond to threats before they escalate. Learn more at borgsecurity.io.
Yes. Borg offers complete post-audit support, including mitigation assistance, patch validation, and re-testing. Their team works directly with your engineers to implement fixes and verify security hardening. This ensures threats are fully neutralized—not just identified.
Borg Security supports projects at any stage, from MVPs to enterprise-grade DeFi platforms. They customize engagements based on project scope, infrastructure, and risk profile. Startups benefit from early threat modeling, while mature platforms use Borg to test advanced scenarios. Contact them at borgsecurity.io to discuss your security needs.
You Might Also Like