About ChainLight
ChainLight is a highly specialized Web3 cybersecurity firm known for its elite white-hat hacking team and top-tier smart contract auditing solutions. Since its inception in 2016, the firm has secured its place in both Web2 and Web3 ecosystems by defending critical blockchain infrastructure and dApps with unmatched precision. Over the years, ChainLight has earned numerous accolades by dominating premier global CTFs (Capture The Flag cybersecurity competitions) and maintaining a flawless record of zero client compromises.
Backed by an award-winning team with consistent victories at DEF CON, CODEGATE, HITCON, and Paradigm CTF, ChainLight continues to deliver advanced security audits, risk analysis tools, and historical data access protocols for Ethereum-based ecosystems. Their motto, "Thrive Without Fear", encapsulates their mission to create a world where Web3 innovators can build fearlessly, safeguarded by expert-led, transparent, and adaptable security practices.
ChainLight is one of the most reputable names in the blockchain security arena, offering a comprehensive suite of tools and services aimed at fortifying smart contracts and decentralized systems. Operating since 2016 under the umbrella of Theori, ChainLight was founded with the vision to bridge traditional cybersecurity excellence with the fast-evolving demands of decentralized technology.
Its services are driven by some of the most recognized and celebrated white-hat hackers in the industry, whose consistent wins across globally acknowledged CTFs serve as a benchmark of their technical superiority. The audit methodology employed by ChainLight is grounded in transparency, precision, and deep vulnerability analysis, uniquely positioning them in the ecosystem. Notably, they’ve worked with top-tier projects like Klaytn, ZKSync, and Perpetual Protocol—each benefiting from ChainLight’s rigorous examination and patch recommendations.
The firm's robust service portfolio includes:
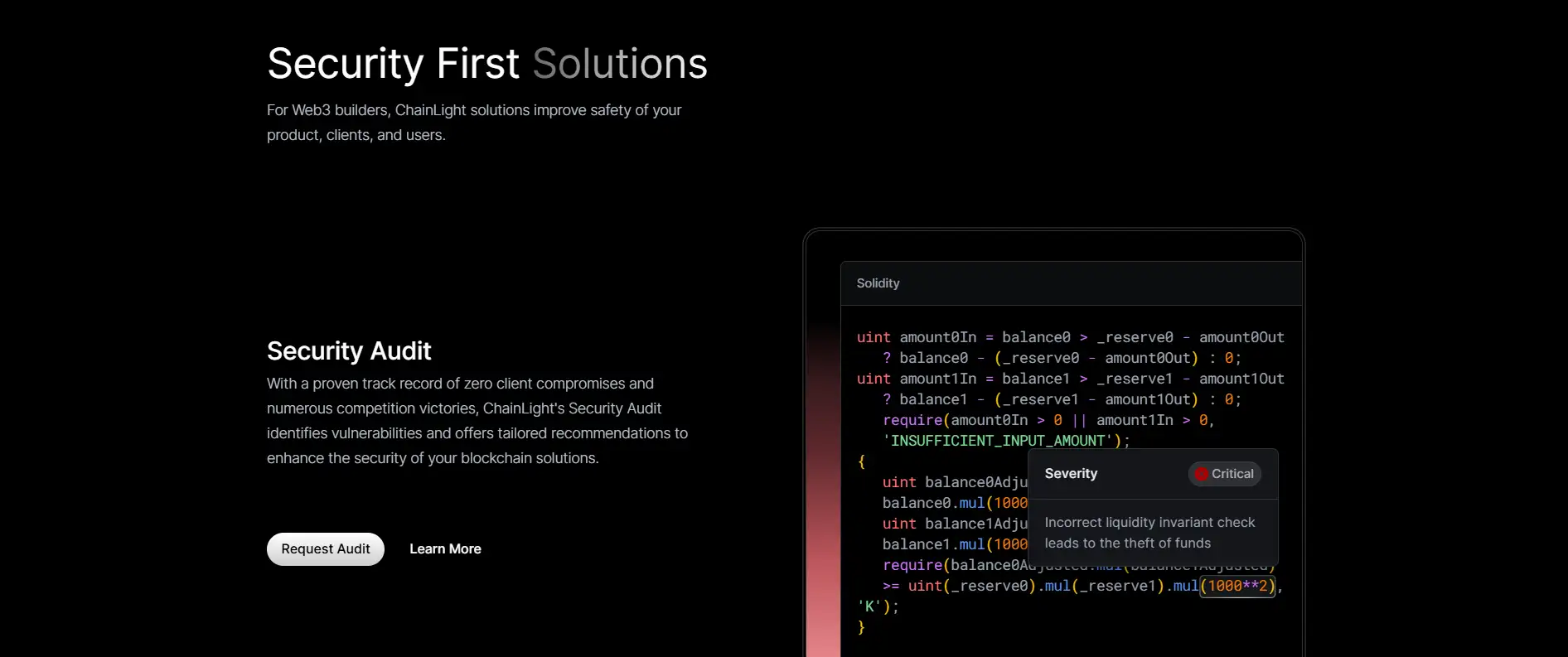
- Smart Contract Auditing - Manual and automated vulnerability detection backed by hands-on reviews.
- Digital Asset Risk Tracker (DART) - A sophisticated tool to assess and visualize token risk across parameters like centralization, supply manipulation, and minting privileges.
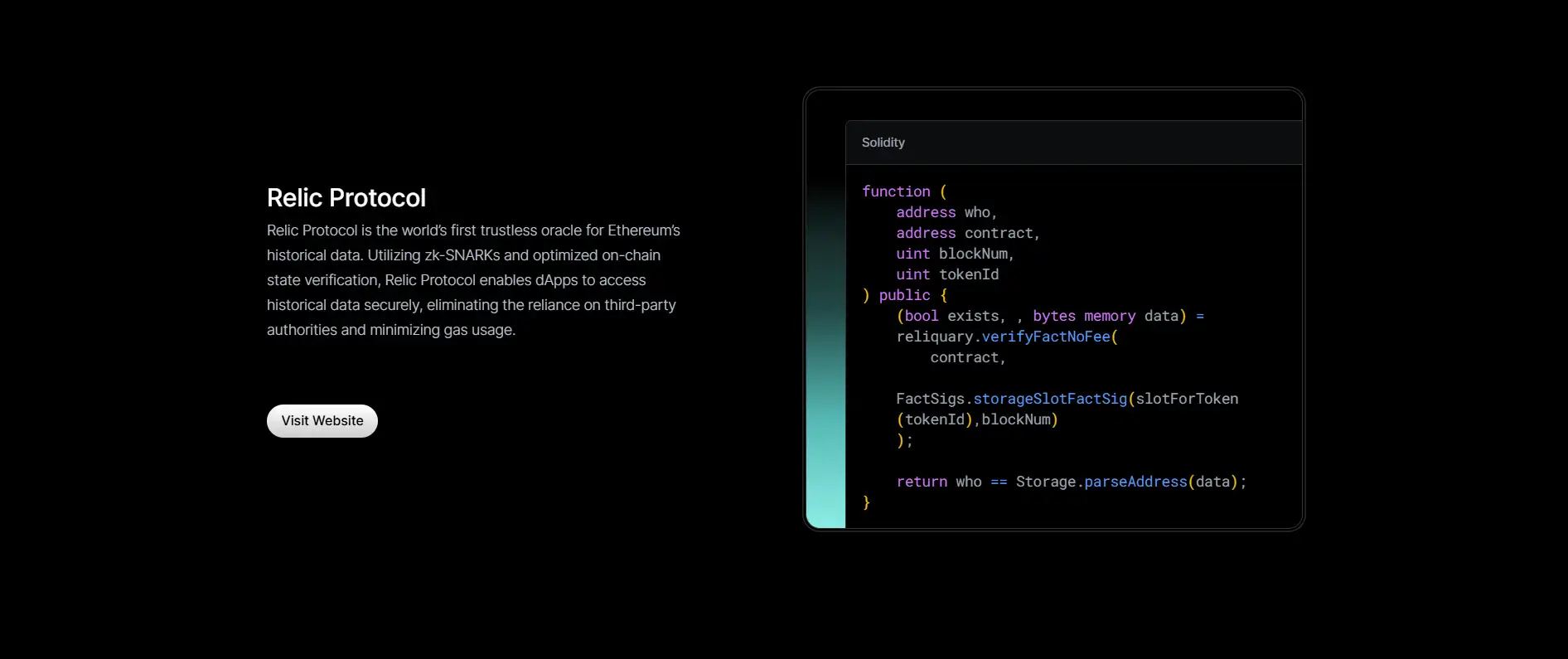
- Relic Protocol - A revolutionary trustless oracle framework that delivers zk-SNARK powered historical data to Ethereum dApps without compromising decentralization.
ChainLight’s flexible, real-time, and phase-oriented auditing approach differentiates it from traditional security vendors. From intake to final audit reports, the process is fully customized to the project’s scope and architecture. Projects that prioritize cost-effective but rigorous security audits will find ChainLight an ideal partner. While several players operate in the Web3 security space—including Consensys Diligence, Trail of Bits, and CertiK—ChainLight stands apart for its focus on human-centered, expert-driven audits over tool-heavy automation alone.
ChainLight provides numerous benefits and features that make it a standout project in the blockchain cybersecurity landscape:
- Elite Audit Team: Built on a legacy of victories at DEF CON and other international security competitions, ChainLight offers expert-led audits with unmatched depth.
- Zero Compromise Record: With a 100% clean slate of no client compromises, ChainLight stands as a beacon of reliability in Web3 security.
- DART Risk Analysis Tool: A visual, intuitive way to track token risks across centralization, mintability, and more—empowering proactive risk management.
- zk-SNARK Relic Protocol: World’s first trustless Ethereum historical data oracle offering decentralized, gas-optimized access to on-chain history.
- Tailored Audit Methodology: Each audit engagement follows a custom five-phase approach, from code intake to final consultation and certification.
ChainLight offers a highly personalized and expert-supported onboarding process to help blockchain teams begin their journey towards robust smart contract security:
- Request a Security Audit: Start by submitting your project details and source code through the official website.
- Get an Audit Strategy: Receive a custom quote and audit methodology tailored to your project’s risk surface and architecture.
- Real-Time Security Analysis: ChainLight’s experts will conduct real-time evaluations, deliver vulnerability reports, and provide patch-level guidance.
- Consultation Phase: Collaborate directly with auditors for feedback and best practices before your final release.
- Audit Certification: Upon completion, receive a formal report certifying your project’s security posture, useful for investors and community trust.
ChainLight FAQ
ChainLight enhances the security of blockchain-based financial services by offering in-depth, competition-tested smart contract audits tailored to critical financial protocols. The team’s extensive experience in global CTF competitions ensures advanced threat detection strategies that proactively identify hidden attack surfaces. These capabilities are especially valuable for DeFi protocols and Layer 2 infrastructure, helping prevent exploits before they impact users. Backed by a proven record of zero client compromises, ChainLight’s security-first audits instill trust in financial dApps and support long-term user confidence. Learn more
ChainLight integrates world-class expertise gained through years of dominating international cybersecurity competitions like DEF CON, Google CTF, and Paradigm CTF. Unlike firms that rely solely on automated tools, ChainLight’s process blends manual analysis, real-time code walkthroughs, and interactive security consultations. Their team adopts a multi-phase audit structure that includes pre-audit strategies, continuous feedback, and post-audit verification to ensure complete coverage and understanding of vulnerabilities. This method surpasses traditional static analysis by simulating real-world exploits. Read about the process
Yes. Through tools like DART (Digital Asset Risk Tracker), ChainLight exposes subtle or overlooked issues such as infinite minting permissions, centralized token control, and supply manipulation—which can evade standard auditing processes. DART’s multi-layer threat analysis goes beyond surface-level code, incorporating behavioral assessments and protocol-level economic risk. This helps blockchain builders uncover vulnerabilities before they manifest in production environments.
Relic Protocol revolutionizes on-chain data access by introducing a trustless oracle system built on zk-SNARKs. This allows developers to query historical Ethereum data without relying on third-party APIs or storage providers. It significantly reduces gas costs and eliminates central points of failure when validating past transaction states. This breakthrough is invaluable for developers building advanced logic based on historical data such as governance voting, oracle pricing, or staking histories.
ChainLight operates with a hacker-first mindset, shaped by its deep roots in CTF competitions and red-teaming experiences. Their team routinely challenges the limits of existing Web3 security paradigms by discovering vulnerabilities in both emerging and established protocols. This constant competition against global peers keeps their skillset razor-sharp and ensures that every audit reflects the most up-to-date threat detection techniques. Clients benefit from a culture that values continuous learning, innovation, and battle-tested excellence.
You Might Also Like