About KelVPN
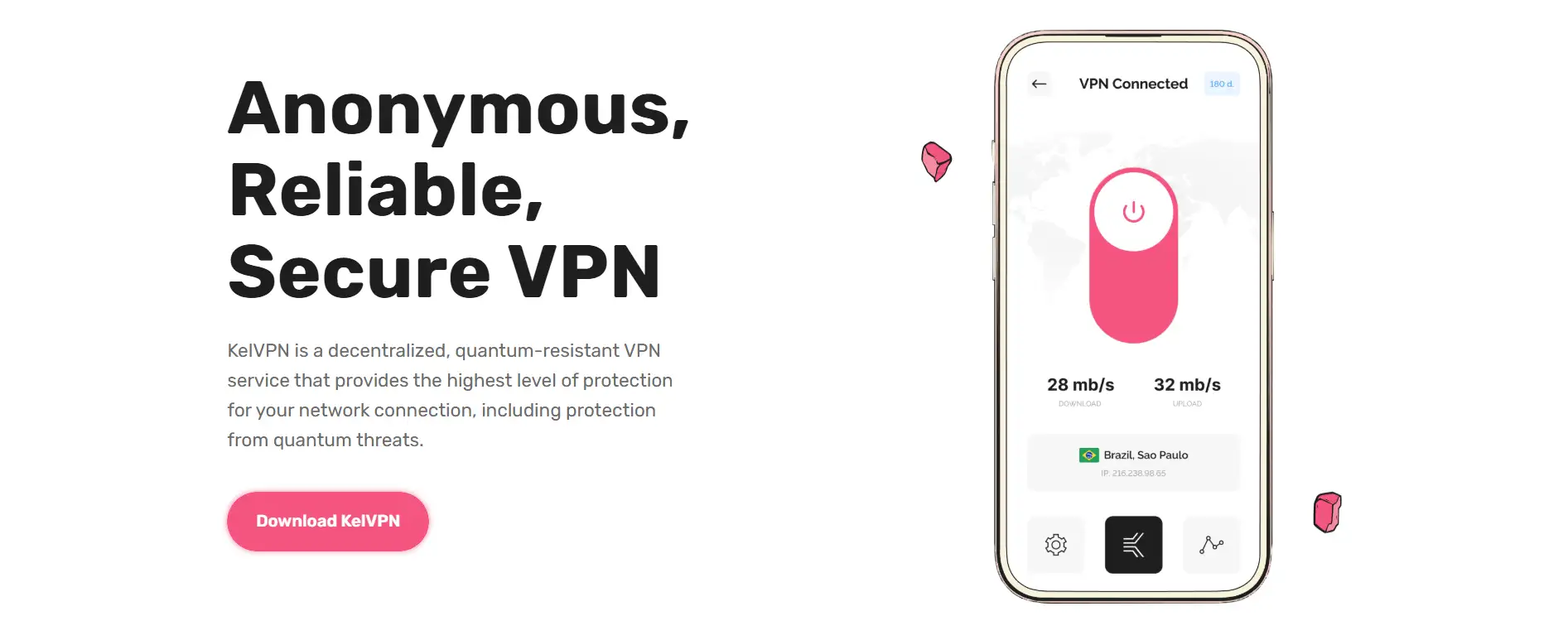
KelVPN is a next-generation decentralized VPN built on blockchain technology to deliver quantum-resistant, anonymous, and secure online communication. Developed as part of the Cellframe Network ecosystem, KelVPN provides users with complete privacy protection, eliminating any need for centralized control or data collection. It ensures that no personal information is gathered, stored, or monitored during use.
Unlike traditional VPNs that rely on centralized servers, KelVPN’s architecture is distributed, leveraging a robust peer-to-peer node network that guarantees high-speed access and immunity against censorship and surveillance. The platform integrates advanced post-quantum encryption technologies to safeguard users from emerging cyber threats, including those posed by future quantum computing advancements. With support for multiple platforms and a strong focus on user accessibility, KelVPN is positioning itself as a crucial solution in the evolving digital privacy landscape.
KelVPN is a pioneering force in the world of secure digital communications, built to offer more than just privacy — it provides a vision for the future of decentralized, censorship-resistant access to the internet. At its core, KelVPN is part of the broader Cellframe Network, which is a blockchain-based ecosystem designed for quantum resistance and high-performance decentralized applications. This affiliation grants KelVPN the technical infrastructure to deliver a powerful VPN solution that not only protects data but also ensures resiliency against threats of all kinds — including quantum computing threats.
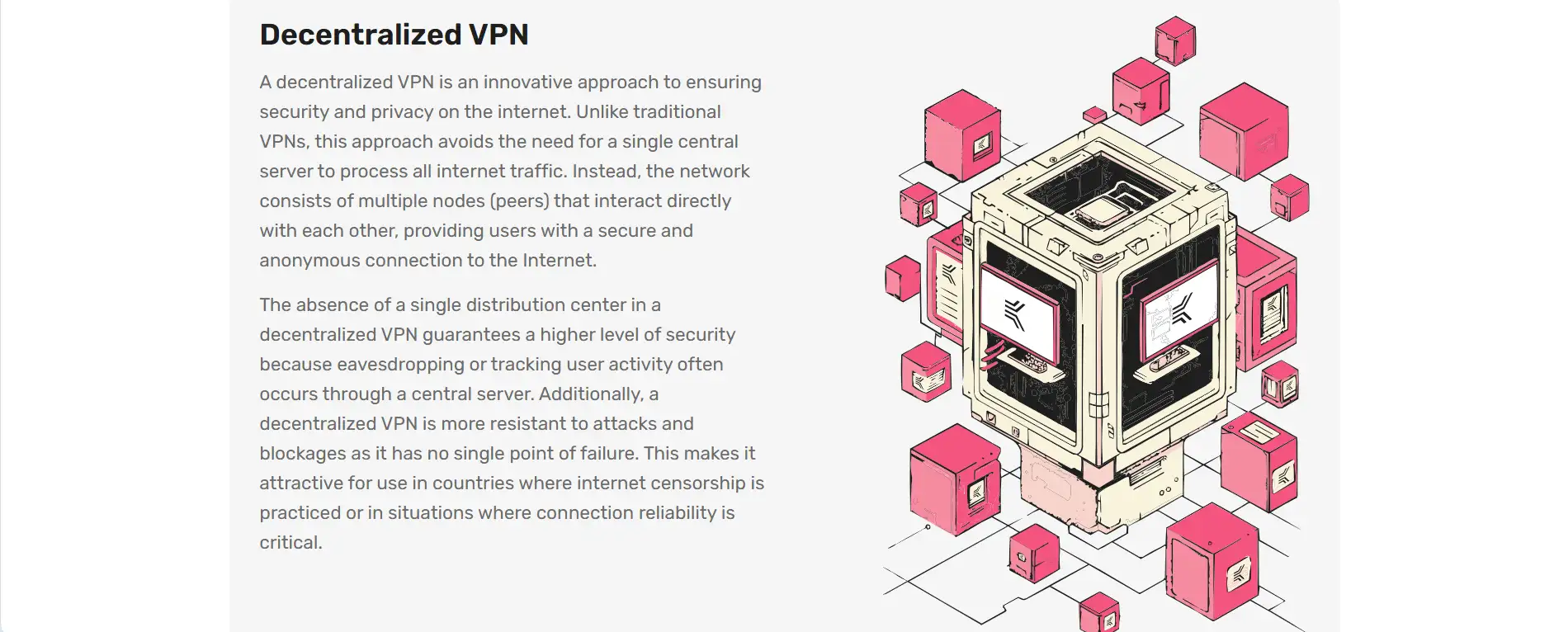
One of the most distinct elements of KelVPN is its use of a node-based architecture that removes the need for centralized servers. Instead, traffic is routed through blockchain-powered nodes that act as secure gateways. This model increases network stability, makes censorship almost impossible, and empowers users to become providers themselves. Unlike traditional VPNs, KelVPN nodes contribute to the blockchain’s operation, which includes validating transactions and hosting access points. Providers earn income by staking KEL tokens and participating in the network — an effective incentive system that promotes participation and decentralization.
The platform is supported across multiple desktop and mobile operating systems, including Windows, Linux, macOS, and Android, with iOS development underway. Users benefit from total anonymity, a proprietary DAP SDK VPN protocol, and high-speed, geographically distributed access points. KelVPN also embraces flexible pricing with competitive rates and support for crypto payments, including its native token. This user-first design is paired with open-source transparency and developer-friendly infrastructure.
Among its contemporaries, KelVPN competes with projects such as Mysterium, Sentinel, and Orchid. However, what sets KelVPN apart is its seamless integration into a larger blockchain ecosystem, quantum-resistant technologies, and the unique ability for any user to operate a node with minimal hardware requirements.
KelVPN provides numerous benefits and features that make it a standout project in the VPN and cybersecurity landscape:
- Quantum-Resistant Security: Utilizes cutting-edge encryption protocols like CRYSTALS-Dilithium and Kyber 512 to guard against current and future quantum threats.
- True Anonymity: No emails, passwords, or cookies are required — ensuring users stay truly anonymous while browsing the internet.
- Decentralized Architecture: A distributed network of blockchain nodes ensures there is no central point of failure and enhances resistance to censorship.
- Income Opportunities: Users can become KelVPN node providers and earn passive income by staking KEL tokens and hosting VPN endpoints.
- Flexible Payments: VPN subscriptions can be purchased using crypto or debit/credit cards, making access easier and more user-friendly.
- Cross-Platform Availability: Works seamlessly on Windows, Linux, macOS, and Android, with iOS support in progress.
- Custom VPN Protocol: The DAP SDK protocol supports encrypted connections under HTTP and other protocols, improving compatibility and stealth.
- Scalable & Eco-Friendly: Lightweight code and hardware flexibility allow for easy deployment on low-power devices and improved energy efficiency.
KelVPN offers a smooth onboarding experience for users who want to start browsing securely within minutes:
- Step 1: Download the App — Visit the official download page and choose your preferred platform: Windows, macOS, Linux, or Android. iOS support is coming soon.
- Step 2: Install the Software — Follow the installer instructions specific to your OS. No email or account creation is required.
- Step 3: Purchase an Access Key — Navigate to the pricing page and select a subscription plan. Pay with KEL tokens or other supported methods.
- Step 4: Connect — Choose a server location from the global list and establish a secure, anonymous connection.
- Optional: Become a Node Provider — For users looking to earn with KelVPN, visit the official site and follow instructions to set up a provider node using minimal hardware and a public IP address.
- Support & Resources: Refer to the KelVPN Wiki or Contact Support for help, FAQs, and community links.
KelVPN FAQ
Yes, KelVPN’s lightweight architecture and optimized low-level C code enable node deployment even on minimal hardware like a Raspberry Pi. This makes it accessible for individuals who want to become providers without investing in expensive equipment. The only technical requirements are a stable internet connection and a public IP address. You can get started by following the instructions on the official KelVPN website.
KelVPN uses a system of “checks” and conditional transactions to authorize and process payments without collecting personal data. Instead of requiring emails or passwords, users generate a check when subscribing to a service. This check is signed by both the user and the node provider, verifying the agreement while maintaining 100% anonymity. This system is already integrated into the blockchain layer via smart contracts and ensures full payment traceability without compromising user privacy. More details can be found on the KelVPN website.
Conditional transactions are a cornerstone of KelVPN’s decentralized payment framework. They allow users to pre-load funds into the system and allocate them to different services over time. Instead of manually processing every transaction, a user can specify conditions and spend slowly, enhancing convenience and ensuring that the VPN remains uninterrupted even during service renewals or provider changes. These transactions are handled at the blockchain level, making them fast, secure, and anonymous. Learn more at KelVPN’s official page.
Yes, KelVPN provides the ability to create your own white-label VPN service using their network infrastructure. This allows entrepreneurs or developers to launch a branded VPN without managing hardware, servers, or system administrators. You just need to focus on marketing, payments, and KEL token usage. All backend operations like traffic routing, encryption, and billing logic are handled by KelVPN’s robust ecosystem. Explore how to get started at KelVPN’s website.
KelVPN is one of the few VPNs that already implements post-quantum cryptographic algorithms such as CRYSTALS-Dilithium for encryption and Kyber 512 for key exchange. These are not just theoretical—they are actively used in securing user data. While most VPNs plan for future upgrades, KelVPN has already embedded these protocols, ensuring that users are protected from quantum attacks today. For more technical insights, visit KelVPN's official site.
You Might Also Like