About Marlin Protocol
Marlin Protocol is a decentralized infrastructure protocol that brings verifiable computation to Web3 through trusted execution environments (TEEs). It enables developers to scale blockchain applications by offloading complex operations to secure off-chain processors without compromising trust or decentralization. Whether for artificial intelligence, DeFi, or decentralized frontends, Marlin provides a flexible and cost-effective way to execute demanding workloads.
Designed for performance, privacy, and modularity, Marlin offers two core compute layers—Oyster CVM (Confidential Virtual Machines) and Oyster Serverless—that allow developers to deploy secure backends, off-chain oracles, coprocessors, or zk-proof generation tools. These compute resources are compatible with smart contracts and web2 endpoints, bridging the gap between on-chain logic and off-chain computation. Marlin makes building next-generation, decentralized cloud applications easier than ever.
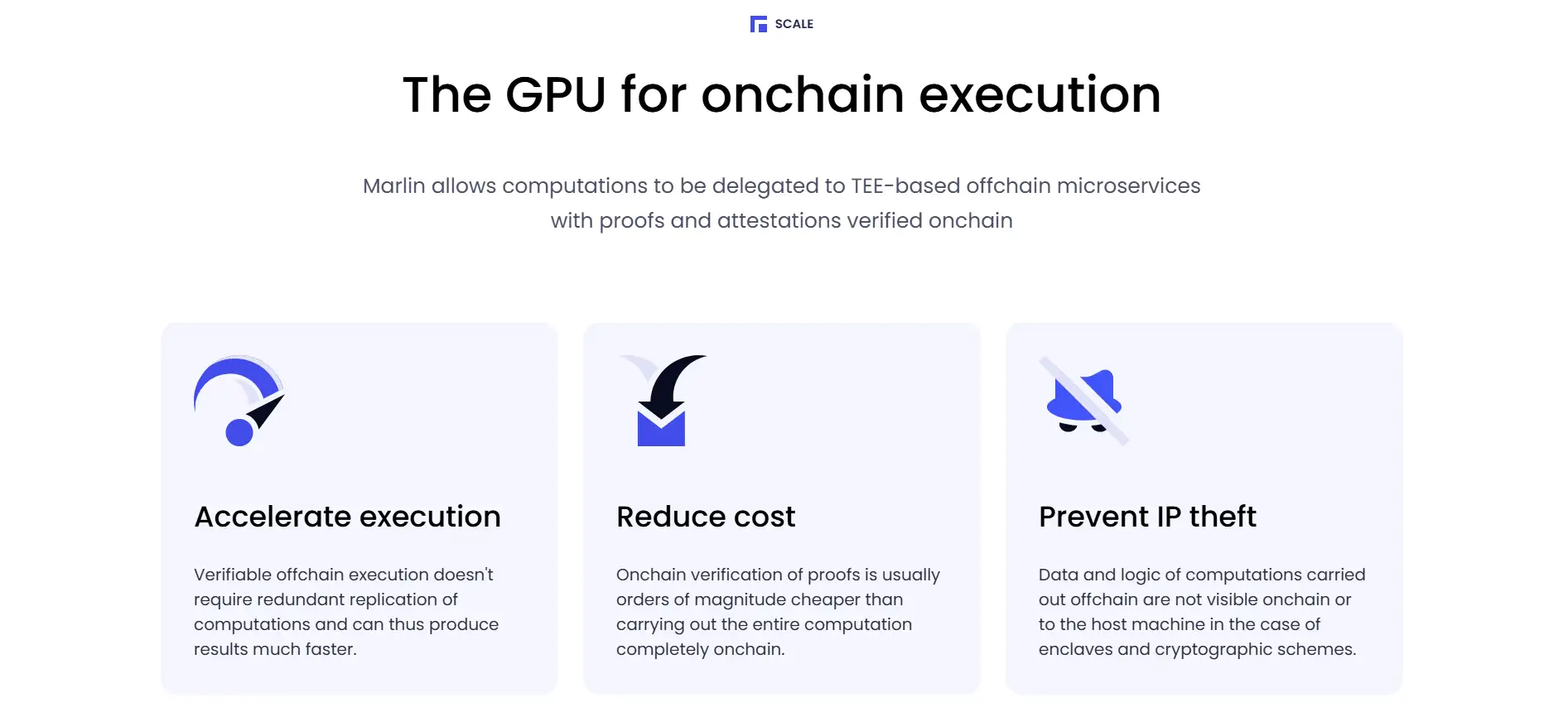
Marlin Protocol redefines decentralized computing by introducing a flexible, modular compute layer that can be used as a trustless coprocessor across blockchain networks. The protocol leverages Trusted Execution Environments (TEEs) to securely run code off-chain while enabling on-chain verification of computation results. This offers a major advantage over traditional on-chain computing and zero-knowledge proofs by significantly reducing costs and latency, all while maintaining security guarantees.
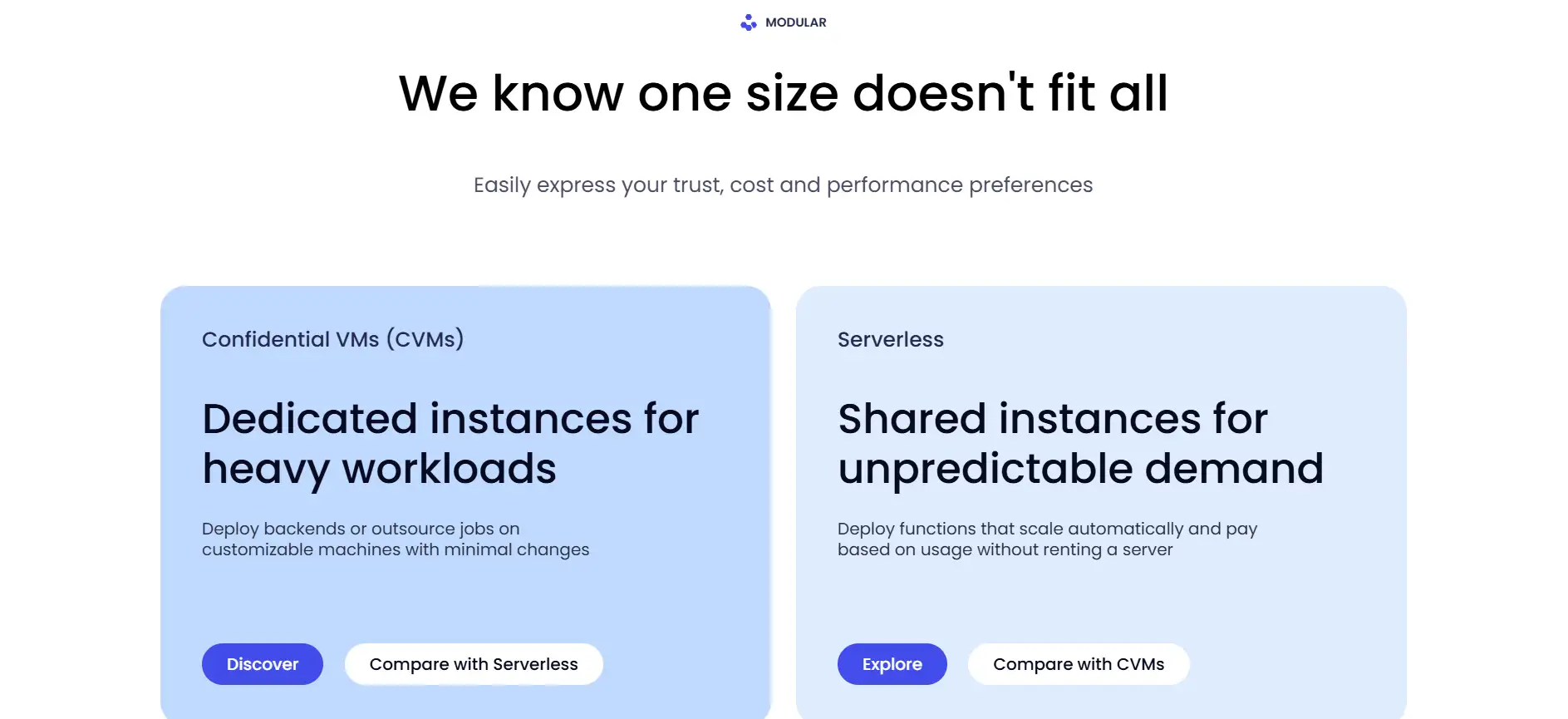
The compute network is branded as Oyster, and it includes two main offerings: Oyster CVM, which provides dedicated Linux-based confidential instances with full hardware access, and Oyster Serverless, a dynamic environment for auto-scalable, short-lived functions. This dual-approach enables Marlin to serve a wide range of use cases—from AI model deployment and data indexing to on-chain automation, DAO tooling, and zk proof marketplaces like Kalypso.
Marlin also powers decentralized MEV infrastructure with mev-bor, a Flashbots-compatible client for Polygon PoS. Moreover, its Relay Network acts as a blockchain-agnostic messaging layer that allows off-chain services to interact seamlessly with smart contracts. With integrations for AI, DEXs, Oracles, and decentralized gateways, Marlin is becoming the default compute substrate for trustless apps.
What sets Marlin apart from platforms like ABR or Cartesi is its full-stack, privacy-first architecture. Unlike traditional off-chain computation platforms that rely on centralized nodes, Marlin’s TEEs ensure data confidentiality, tamper-resistance, and deterministic reproducibility. Whether you're running inference on large language models or triggering a DeFi liquidation bot, Marlin ensures verifiability and auditability across workloads.
In addition, Marlin supports open participation. Anyone can become a node operator using Intel SGX, AWS Nitro, or NVIDIA GPUs with confidential computing. Developers can build, test, and deploy workloads using familiar tools like Docker, Rust, and Python, while interacting with the network through smart contracts or RESTful APIs. The project is backed by major investors like Binance Labs, Arrington Capital, and Electric Capital, ensuring both funding and credibility.
Marlin Protocol introduces a number of advanced features that distinguish it in the decentralized compute space:
- Confidential Compute: Leverages TEEs like Intel SGX and AWS Nitro Enclaves to execute code privately and securely, protecting both data and logic from external access.
- Oyster CVM and Serverless: Two execution models to suit both persistent, heavy workloads and dynamic, short-term functions.
- Multi-chain Relay Network: Offers a blockchain-agnostic message layer to relay computation results to any chain, enabling real-time off-chain services for dApps.
- zk + TEE Hybrid: Use TEEs for heavy processing and zero-knowledge proofs for verification, optimizing both performance and trust.
- Plug-and-Play Infrastructure: Developers can deploy backend logic via Docker, use REST APIs, or call smart contracts to execute off-chain code.
- AI & ML Integration: Train and deploy verifiable machine learning models using Oyster, with privacy for both models and user inputs.
- DeFi and DAO Automation: Automate liquidation bots, governance actions, or price tracking through off-chain services linked to on-chain contracts.
- Interoperability: Supports interactions with Ethereum, Arbitrum, Polygon, and more, abstracting away the underlying blockchain for developers.
Getting started with Marlin Protocol is designed to be developer-friendly and modular. Here's how to begin building:
- Visit the official site: Start at Marlin.org to explore the ecosystem, read documentation, and join the community.
- Explore Oyster Serverless: Use Marlin Hub to deploy short-lived serverless functions that scale automatically. Pay only for execution time.
- Use Oyster CVM for heavy workloads: Deploy confidential virtual machines with Docker. Gain access to full TEE environments with reproducible builds and secure key storage.
- Leverage Relay Contracts: Integrate on-chain relay contracts to receive computation results from off-chain services securely.
- Access Dev Tools: Use GitHub libraries, APIs, Solidity contracts, and CLI tools to interact with Marlin nodes and enclaves.
- Try AI & zk Demos: Deploy an LLM like Llama2 on Oyster or use Kalypso to sell zero-knowledge proofs on a permissionless marketplace.
- Join as a node operator: Contribute compute by setting up a TEE-enabled node. Both CPUs and GPUs are supported depending on workload.
Marlin Protocol FAQ
Marlin’s Oyster protocol uses Trusted Execution Environments (TEEs) to provide a secure and private off-chain computing environment, which is tamper-resistant and prevents node operators from snooping on the computation or data. Unlike other decentralized compute platforms that rely on standard server nodes, Oyster ensures confidentiality, integrity, and verifiability by using hardware-level isolation combined with on-chain attestations. This means developers can offload complex tasks without sacrificing security or decentralization.
Yes. Marlin supports confidential AI model execution through Oyster. Both the model architecture and the input data remain private, even from the node operators executing them. This is enabled via TEEs, which isolate the runtime environment and provide strong privacy guarantees. Developers can deploy models using Docker and access them through REST APIs or smart contracts, enabling secure ML inference in a decentralized environment.
Oyster CVM (Confidential Virtual Machines) offers dedicated TEE instances that are rented per deployment, ideal for long-running or resource-heavy tasks. In contrast, Oyster Serverless allows users to deploy lightweight functions that auto-scale and only incur cost for the time executed. Serverless is more flexible for unpredictable workloads and requires no manual provisioning. CVMs provide full Linux environments while Serverless runs isolated JS/WASM functions.
No. One of the strengths of Marlin Protocol is its support for popular developer tools and languages. You can use Python, Rust, Go, C++, or even import existing web2 applications into Docker containers. The platform supports standard web frameworks, Rust crates, and even machine learning libraries. This makes the transition seamless for developers who want to build scalable and verifiable apps without having to learn custom VMs or domain-specific languages.
Marlin uses a combination of hardware attestation and on-chain verification to guarantee that computations are performed correctly in trusted environments. Each TEE enclave provides an attestation that proves the code and environment used. These attestations are publicly verifiable using tools like RISC Zero and Marlin’s Solidity libraries. This ensures that results can be trusted even when performed off-chain—without relying on centralized validators or trusted third parties.
You Might Also Like