About Sherlock
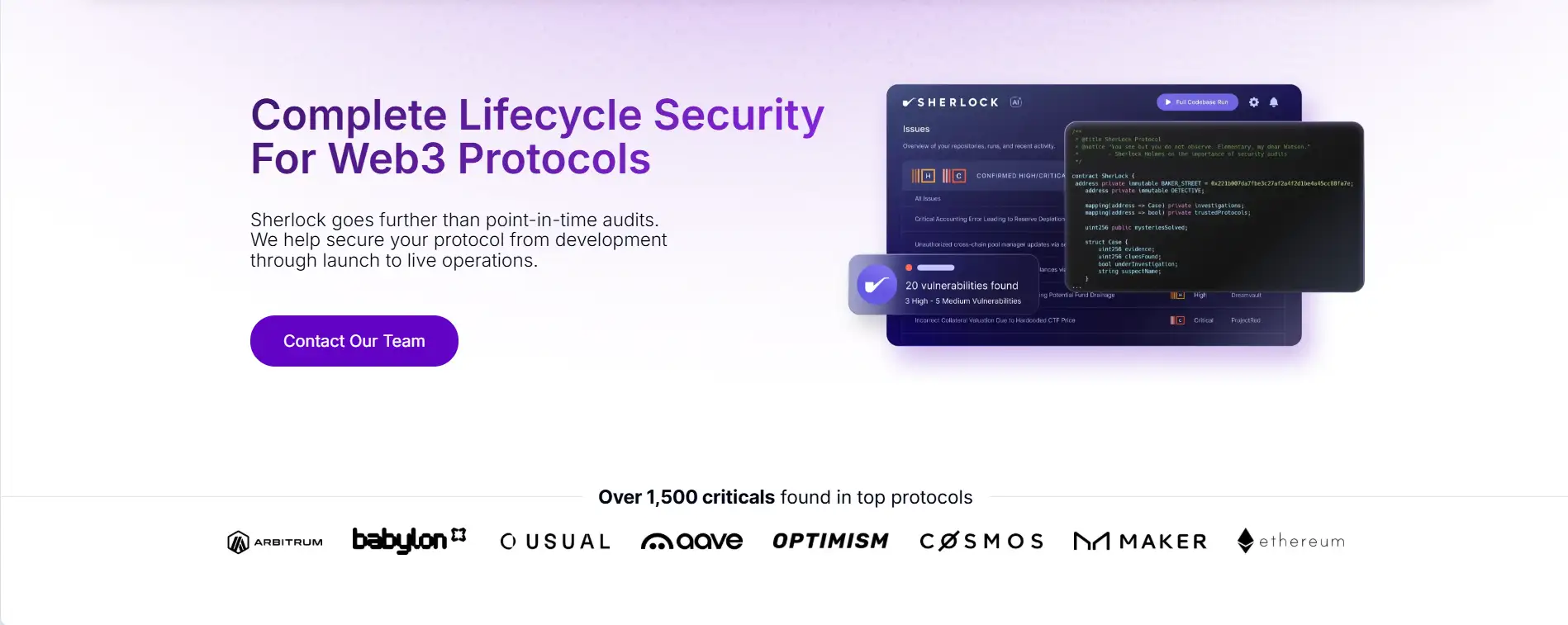
Sherlock is a comprehensive Web3 security platform that secures protocols throughout their entire lifecycle—from development to deployment and beyond. Unlike traditional audit firms that offer one-time security reviews, Sherlock provides ongoing protection through a unified system combining collaborative audits, audit contests, AI analysis, bug bounties, and exploit coverage. This integrated model ensures that vulnerabilities are not just found—they’re prevented, mitigated, and covered.
By combining a community of top-ranked security researchers with powerful AI tooling and a well-tested coverage protocol, Sherlock offers protocols the most reliable and scalable approach to smart contract security. Whether you're just starting development or managing a billion-dollar DeFi ecosystem, Sherlock adapts to your needs with industry-leading precision and trust.
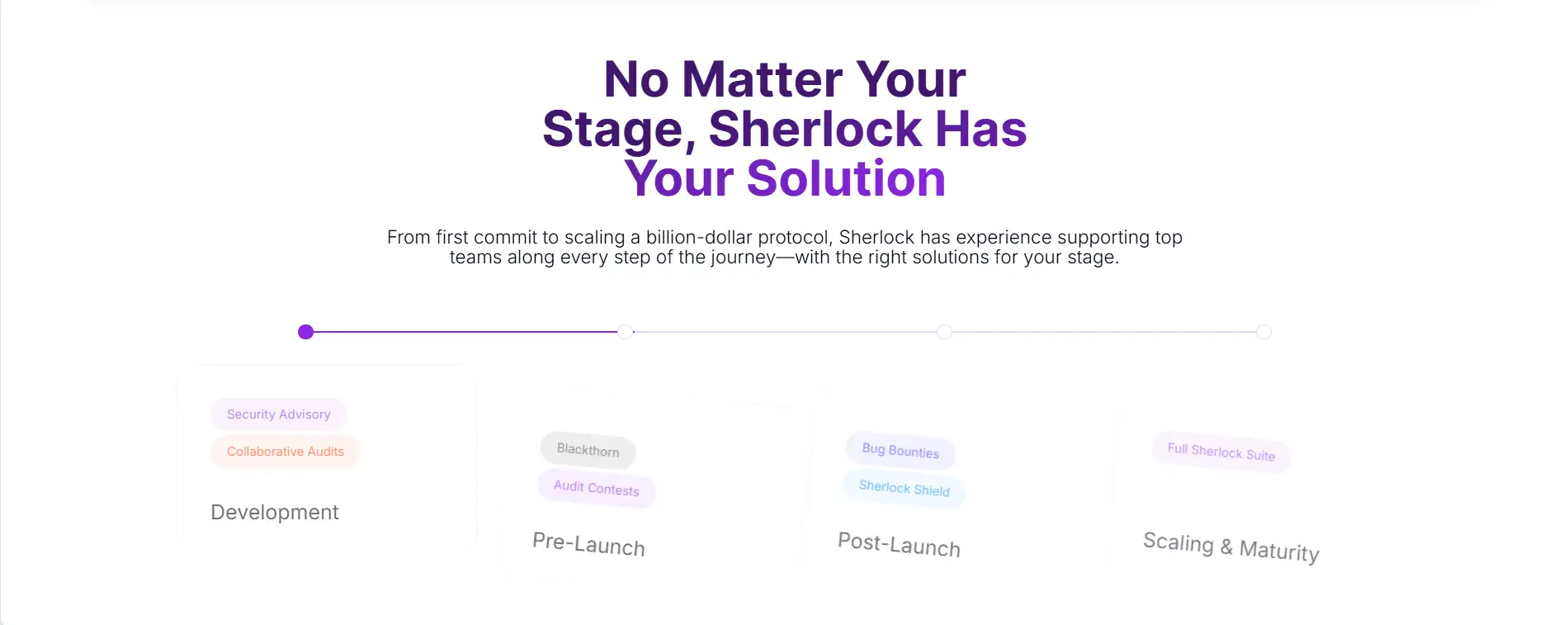
Sherlock was created to revolutionize how Web3 protocols approach security by making protection a continuous, integrated part of the development lifecycle. Traditional audits often fall short due to time constraints, evolving codebases, and reactive practices. Sherlock introduces a proactive model that connects every phase of protocol security under one unified system.
At the foundation is Sherlock AI, an AI-powered auditing assistant that integrates directly into a team’s development workflow. By analyzing code as it’s written, Sherlock AI enables teams to identify and fix vulnerabilities in real time—without waiting for a post-development audit cycle. This tool helps protocols stay on budget and meet deadlines while embedding security from day one.
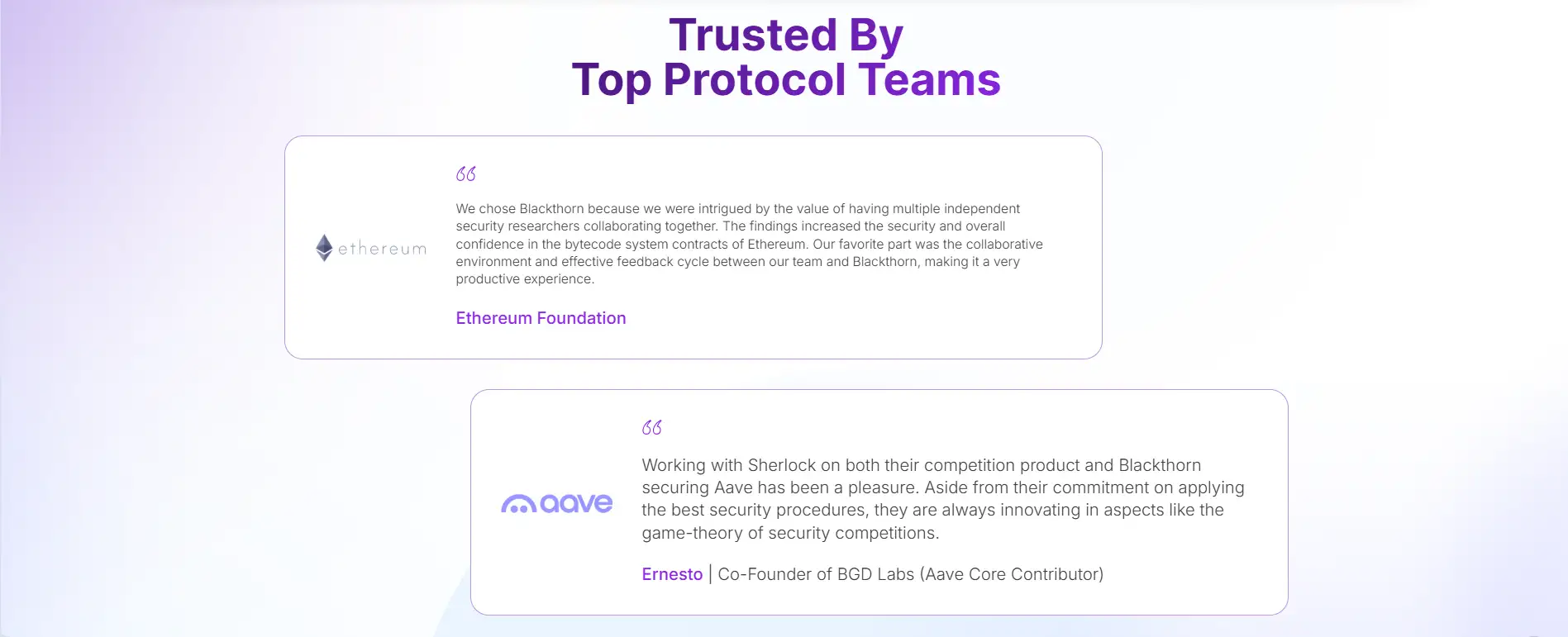
In parallel, Sherlock’s Collaborative Audits bring together the best security researchers in crypto to conduct in-depth manual audits. Unlike single auditor models, Sherlock’s collaborative process ensures findings are cross-reviewed and peer validated, reducing the risk of missed criticals. This model has earned the trust of leading protocols and investors across Web3.
To push the boundaries of quality and competitiveness, Sherlock Audit Contests invite elite smart contract researchers to compete in securing code. These time-boxed events have surfaced thousands of vulnerabilities that might have otherwise gone unnoticed, reinforcing Sherlock’s reputation as a leader in competitive security discovery. In fact, Sherlock ranked #1 in Audit Contests in both 2023 and 2024.
Once a project is live, Bug Bounties and Sherlock Shield provide continuous protection. Sherlock’s bug bounty platform has been refined over years to reduce noise by more than 100x compared to traditional programs, ensuring only quality reports reach protocol teams. Every project audited by Sherlock also gets access to exploit coverage via Sherlock Shield, offering financial protection against critical exploits—something few providers in Web3 offer.
Compared to firms like CertiK, SlowMist, and Hacken, Sherlock stands out for offering full lifecycle protection, elite researcher collaboration, and actual exploit coverage. Instead of being limited to audits or bug bounty hosting, Sherlock brings all components together for security that evolves with your protocol.
Sherlock provides numerous benefits and features that make it a unique force in the Web3 security industry:
- AI-Powered Development Security: Sherlock AI offers real-time vulnerability detection directly in the development workflow, reducing reliance on post-build audits.
- Collaborative Manual Audits: Engage top-ranked auditors working together under a rigorous peer-reviewed system to uncover and validate vulnerabilities before launch.
- Elite Audit Contests: Open your code to competitive researchers from Sherlock’s leaderboard and identify critical flaws others might miss.
- Noise-Free Bug Bounties: Attract top bug hunters with a platform that reduces false positives by over 100x, giving your team only high-quality findings.
- Sherlock Shield Coverage: Get real post-launch exploit protection. If a critical vulnerability is missed during an audit and exploited, Sherlock pays out.
- Complete Lifecycle Security: From development to post-launch, Sherlock integrates every phase of your protocol's journey into one continuous security flow.
- Top Industry Recognition: Voted #1 in audit contests for two consecutive years and trusted by some of the largest protocols in Web3.
Sherlock makes it easy for Web3 protocol teams to begin securing their projects at any stage of development. Here’s how to get started with Sherlock:
- Step 1 – Visit the Site: Go to the Sherlock homepage to review available services like audits, AI tooling, and bounty coverage.
- Step 2 – Contact the Team: Use the “Contact Our Team” button to schedule a discovery call or request a quote based on your audit or security needs.
- Step 3 – Engage Sherlock AI: Begin integrating Sherlock AI into your development process to catch bugs before your code reaches production.
- Step 4 – Plan an Audit: Work with Sherlock to schedule a collaborative audit or audit contest based on the complexity and timeline of your deployment.
- Step 5 – Launch with Bug Bounties: Add post-launch bug bounty protection to your security stack through Sherlock’s high-signal bounty system.
- Step 6 – Activate Sherlock Shield: Qualify for exploit coverage to mitigate the financial risks of any missed vulnerabilities in production.
Sherlock FAQ
Sherlock AI brings auditor-level analysis directly into the developer workflow, enabling teams to catch vulnerabilities from the first commit. Unlike traditional auditing tools that analyze after development, Sherlock AI operates in real-time, offering insights and alerts during coding. This continuous integration reduces last-minute audit stress and keeps security aligned with product timelines. Learn more at Sherlock's official website.
Unlike siloed audits performed by individual reviewers, Sherlock’s collaborative audit model brings together elite security researchers to work as a team. Findings are peer-reviewed, allowing for higher accuracy and deeper vulnerability detection. This team-based approach is designed to match the complexity of modern smart contracts, offering more resilience than solo reviews. Explore audit options at sherlock.xyz.
Sherlock Audit Contests invite top-ranked security researchers to compete in identifying bugs in smart contracts. This gamified and time-bound model increases motivation and thoroughness, often surfacing vulnerabilities that traditional audits miss. Contestants are ranked and incentivized, ensuring high engagement and rigorous code analysis. Discover how it works at Sherlock’s Audit Contests page.
Sherlock Shield is an exploit coverage program that financially protects protocols audited by Sherlock. If a critical vulnerability slips through and is exploited after launch, Shield can provide payouts based on the terms agreed during onboarding. It acts as a financial safety net for audited code, backed by a rigorous payout process and a team of security experts. Learn more at Sherlock.xyz.
Sherlock’s Bug Bounty platform is optimized for signal over noise. By filtering submissions through its exclusive researcher community and leveraging automated tooling, it reduces false submissions by over 100x compared to traditional bounty systems. This allows protocol teams to focus on real threats without being overwhelmed by low-quality reports. Learn more at Sherlock’s Bug Bounties section.
You Might Also Like